Ghostery is a special browser plugin that will allow you to block cookies from adware, spyware, and tracking services. It’s 100% and focused on helping the average Internet citizen protect themselves from prying eyes.
However, if we turn the tables, Ghostery can be used by marketers to help discover the tools other marketers are using. In this brief post, I’ll show you how to do that and also show you how using Ghostery can protect your own customers.
Download Ghostery
Downloading Ghostery is pretty simple, just pop on over to their site and hit the download link. Right now, Ghostery supports all major desktop browsers as well as iOS (iPhone and iPad) using a special browser app available in the App Store.
Using Ghostery
Once installed, Ghostery will ask you to set up blocking options. If you’re interested in sniffing about other websites, don’t turn on any of these features. This will let Ghostery notify you of tracking cookies dropped when you visit various sites.
Here’s an example of Ghostery in action when visiting Amazon.com:
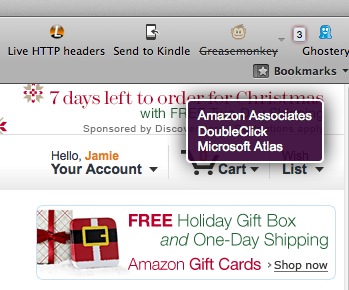
When entering a page, Ghostery will check the scripts and cookies set against its repository and alert you to the “bugs” dropped on your browser. In this case, Amazon is dropping beacons from Amazon Associates, DoubleClick, and Microsoft Atlas.
If I click the little ghost icon in the menu bar, I can drill into each of the found beacons for more information:
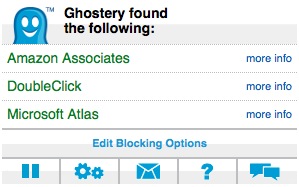
For example, if I drill into Microsoft Atlas, I’ll go to the Microsoft Atlas entry on Ghostery. Here I’ll learn that this script is found on over 60,000 websites and is used for targeted advertising on Microsoft’s online properties.
Protecting the Privacy of Your Customers
Obviously, Ghostery is a powerful tool that makes it easy to find out exactly what your competition is trying, but don’t stop there. You can also use it on your own site to see how your knowledge of the beacons you drop on visitors stacks up against the reality of what’s really going on. You might be surprised by what you find.
For example, you might be trying a new advertising network. Everything looks simple enough. You just drop a little bit of Javascript and you’re serving ads somewhere, right? Well, it may just be that that Javascript loads some additional script and or beacons and suddenly your site is getting flagged for serving malware or spyware. Even worse, you might be exposing your customer’s information in ways you did not expect (nor which you’ve covered in your site’s Privacy Policy).
Not only is this bad business, but it could also spell trouble.

